FBI demand to unlock iPhones draws protest at Hoover Building
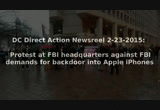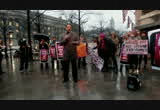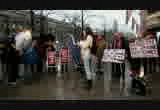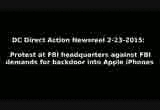
On the 23rd of February, protesters representing groups from Code Pink all the way to the CATO Institute showed up in front of the FBI's J Edgar Hoover building to protest the FBI's demands that Apple help them defeat encrypted iPhones. Speakers emphasized that this is not about one iPhone but all iPhones. Several predicted that if the FBI is sucessful those who steal credit card information would also take advantage of it. A Black Lives Matter speaker emphasized the danger that police surveillance and especially phone snooping poses to their movement. She reminded everyone of the ugly history of COOINTELPRO and racist FBI suppression of people of color. To many in this world, the FBI is not fighting terrorists, they are the terrorists.
Among US Muslims, animal rights activists, and environmental activists alike the FBI is known for creating fake bomb plots from whole cloth, then arresting anyone they can recruit to these phony terror plots. When the FBI claims to have disrupted a terror plot, most of the time the only guns or explosives either were figments of an FBI agent's imagination or were outright provided by the FBI. In addition to FBI fake terrorism, real FBI terrorism takes the form of everything from threats and home/work visits to raids on activist homes, and for the Black Panthers and the American Indian Movement it has even escalated to outright murder and assasination. The FBI is also well known for their role in the siege of the Branch Davidians at WACO and blamed by many for its fiery end. Many people from across the political spectrum have strong reasons never to trust such an agency with a back door into their phones!
The protest at the FBI's Hoover Building was only one of a series of protests across the US. Most were held at Apple stores urging this multibillion dollar company to continue refusing to cooperate with the FBI's demands, and demanding the FBI cease and desist with this brazen assault on people's privacy and security. Later that night, WTOP Radio aired a story confirming that the FBI is not trying to unlock one iPhone only, but actually ten different phones, only one belonging to the San Bernardino/Daesh shooter. There have been stories in other media that the FBI picked the only US case connected to ISIS/Daesh not for investigative reasons given that the defendant is dead, but rather as the case most likely to build public sympathy for the FBI.
Prior to the Snowden revelations, iPhones were known to many in progressive circles as a dangerous security hazard, and for years Apple gladly give police and the FBI anything they wanted. Then came the Snowden revelations, which suddenly made people think twice about where all their data wwas going. With Europe talking of banning their data going to US servers and even Facebook and Google sweating hard, Apple stepped up to the plate and installed encryption by default on all their phones.
On the one hand, just because the FBI claims they can't crack in iPhone today doesn't mean an iPhone used tomorrow at a felony-level direct action will still be secure on the day the 6 year statute of limitations runs out. On the other hand, a brand-new iPhone with encryption by default is a lot easier for a non-techical user to secure than a brand-new Windows XP computer in 2005. That required reinstalling the entire operating system from scratch over an encrypted disk, either Windows over Truecrypt or preferably Linux with its native encryption. Today an iPhone owner who turns off backup to Apple and uses a strong passphrase has a machine that will apparently stop most cops most of the time. When that's not enough, some Android phones with unlocked bootloaders are capable of having Android wiped and replaced with Linux over military-grade full disk encryption.
![]() Video-activists warn true purpose of FBI snooping is to suppress domestic dissent
Video-activists warn true purpose of FBI snooping is to suppress domestic dissent